In today’s complex, fast-moving, technology-enabled business environment, cyber attacks are frequent and increasingly difficult to detect and prevent. After only one quarter, 2021 has had more significant breaches than the entire previous year. You can hardly read the news without coming across a story about another company facing fallout from a breach, ransomware, or some other serious cyber incident.
While attackers have several vectors by which they can gain unauthorized access to their victims’ systems, one that is increasing in popularity and effectiveness is phishing. Phishing emails are a common way attackers take advantage of, or exploit, businesses in order to gain a foothold within them. Once attackers have access to an organization’s systems, the potential damage they can cause to that organization is limited only by your imagination.
Why Is Phishing a Persistent Problem?
Phishing is a type of social engineering that uses carefully crafted emails (or phone scams, fraudulent social media messages, etc.) from malicious actors to mimic emails from legitimate senders, with the goal of tricking recipients into divulging sensitive information. The tactic takes advantage of psychology and our natural human tendencies to respect authority, conform to social norms, and make quick decisions based on cues that have led to successful outcomes in the past, to name only a few. By manipulating victims, phishers often succeed in obtaining valuable data such as passwords, protected health information, credit card numbers, and more.
According to Verizon’s 2021 Data Breach Investigations Report, approximately one-third of data breaches involve phishing or related social engineering tactics, and 85% involve a human element. Because changing human behavior at scale is significantly more complex and difficult than implementing technical controls to protect systems, phishing continues to be a successful attack method and persists as one of the most concerning cyber threats.
How Can You Protect Your Organization?
Phishing emails typically tell a story to get you to take an action: clicking a link, entering personal information, opening a communication channel with the attacker. It is important to understand what you are being asked to do and whether this behavior is expected.
There are things you can do the next time you get an email to protect yourself and your organization from being compromised. Emphasizing a few simple practices to improve your cyber hygiene will put you on the path to becoming a cybersecurity superstar!
Check for Grammatical and Punctuation Errors
Marketers and content creators go to great lengths to create emails directed at a target audience, with incredible attention paid to content, subject line, call to action, etc. Emails that contain poor grammar or punctuation errors are likely from inexperienced attackers. Inadvertent typos do happen, even to legitimate marketers, but multiple errors in the same message often indicate you could be looking at a phishing email.
Evaluate the Content and the Call to Action
Phishing emails are designed to elicit an emotional response in order to get you to perform an action—and are part of a larger attack methodology called social engineering. There are many ways scammers abuse our emotions in order to get us to act in ways that are not in our best interest:
- Keep an eye out for emails with urgent deadlines, typically with warnings and potential consequences.
- The content of the email should never ask you for sensitive information. Legitimate businesses have reputations to uphold and will never ask you for personally identifiable information via email.
- You’ve heard the saying: “If it sounds too good to be true, it probably is.” Emails that offer free rewards, or unsolicited rewards, should be regarded as highly suspicious.
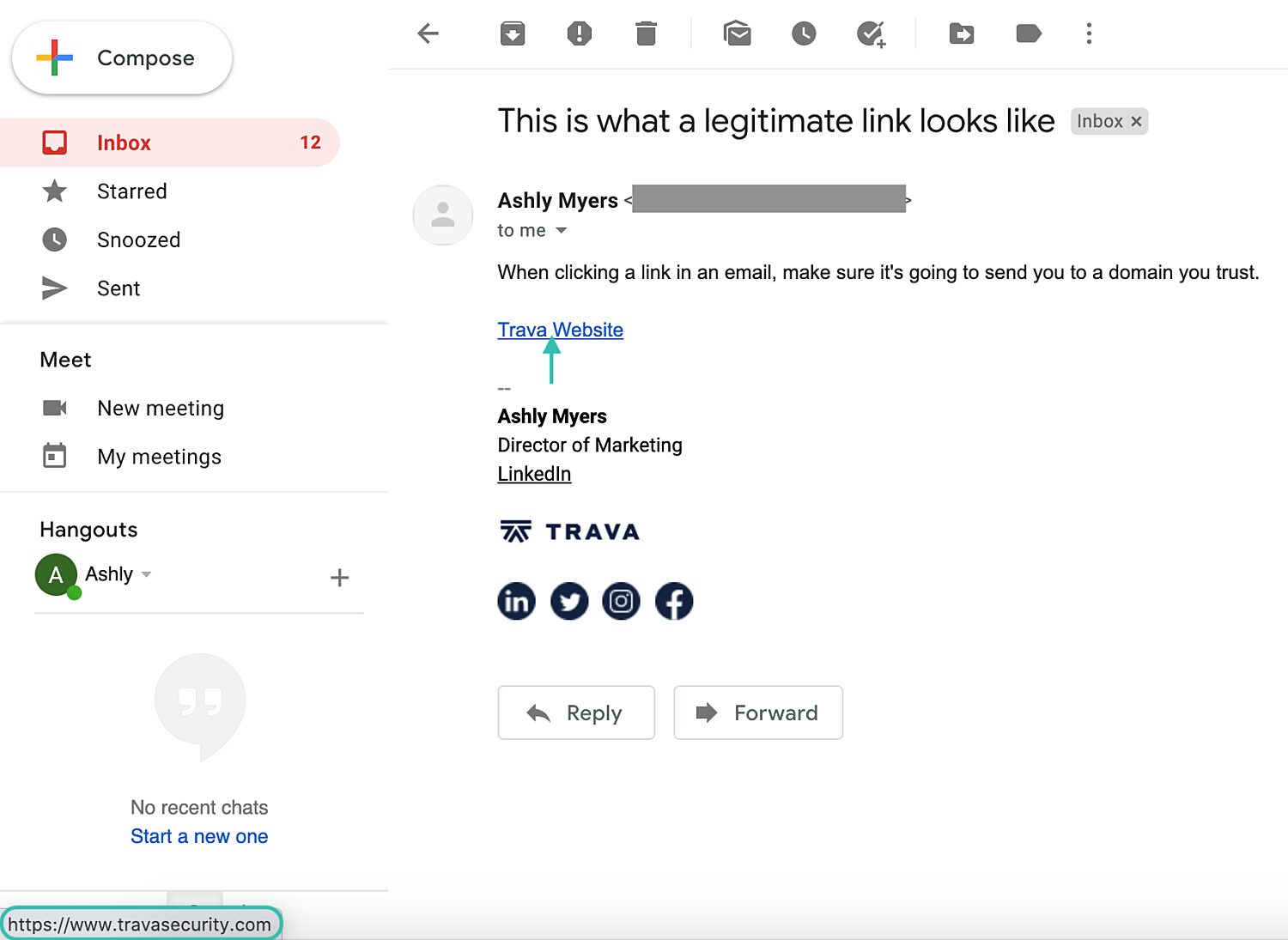
Verify the Link Before You Click on It
When you receive an email with text links or call-to-action buttons, you can hover your mouse over a link or button to get a preview of the destination URL. The preview typically appears in the bottom left of your screen and shows you where you’ll end up if you click through from the email. Be sure that the URL contains a verified domain you trust. If it doesn’t, don’t click the link!